Stuxnet Trojan - Memory Forensics with Volatility | Part I
Stuxnet could be the first advanced malware. It is thought that it was developed by the United States and Israel to attack Iran's nuclear facilities. It attacked Windows systems using a zero-day exploit and It was focused on SCADA systems in order to affect critical infrastructures... Also, it may be spread from USB drivers. It is necessary a squad of highly capable programmers with depth of knowledge of industrial processes and an interest in attacking industrial infrastructure to develop this malware.
Kaspersky Lab concluded that the sophisticated attack could only have been conducted "with nation-state support" and a study of the spread of Stuxnet by Symantec says that it was spread to Iran (58.85%), Indonesia (18.22%), India (8.31%), Azerbaijan (2.57%)....
Thanks to Malware Cookbook we can download a memory dump from an infected host with this malware in the URL below:
Kaspersky Lab concluded that the sophisticated attack could only have been conducted "with nation-state support" and a study of the spread of Stuxnet by Symantec says that it was spread to Iran (58.85%), Indonesia (18.22%), India (8.31%), Azerbaijan (2.57%)....
Thanks to Malware Cookbook we can download a memory dump from an infected host with this malware in the URL below:
http://www.jonrajewski.com/data/Malware/stuxnet.vmem.zip
Ok, let’s go. We are going to analyze it with Volatility.
STUXNET IMAGE INFO
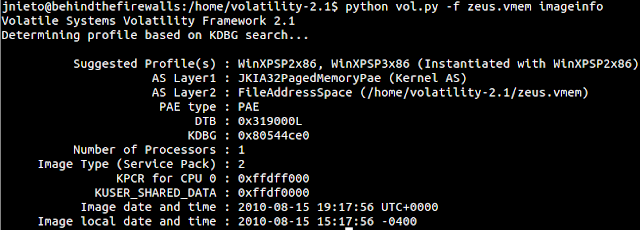
First of all we want to get more info of the memory image. With the command below we can see the volatility suggested profile and when the image was dumped. In this case it was in 2011-06-03.
python2 vol.py -f stuxnet.vmem imageinfo
It is a good practice to export the profile WinXPSP3x86 in order not to specify more this profile in the Volatility commands.
export VOLATILITY_PROFILE=WinXPSP3x86
DETECTING MALICIOUS PROCESS
First of all, I usually want to know what process was running the computer when the memory was dumped.
Notice you will see that three lsass.exe processes were running… It draws our attention.
- lsass.exe Pid 680
- lsass.exe Pid 868
- lsass.exe Pid 1928
python2 vol.py -f stuxnet.vmem pslist
We know that lsass.exe is one of the first processes to start when Windows boots. Because of this, it’s normal that “lsass.exe” has a lower Pid. You can see when the three lsass.exe process started in the picture above:
- Pid 680 started at 2010-10-29 17:08:54
- Pid 868 started at 2011-06-03 04:26:55
- Pid 1928 started at 2011-06-03 04:26:55
You can see the “lsass.exe” with lower Pid (680) started in 2010 and the other ones with higher Pid (868 and 1928) started in 2011. It isn’t a normal behavior.
In the picture below we can notice that Winlogon.exe (Pid 624) started one of the “lsass.exe” process (Pid 680). This is a really good indication of which “lsass.exe” isn’t malicious, because Winlogon.exe always starts the real “lsass.exe”. The “lsass.exe” with Pid 868 and 1928 was started by the “services.exe” process. It isn’t a normal behavior. They could be malicious processes.
python2 vol.py -f stuxnet.vmem pstree | egrep '(services.exe|lsass.exe|winlogon.exe)'
We have just discovered two suspicious processes.
DETECTING MALICIOUS CONNECTIONS
It is really important to indentify if theses suspicious processes were making connections. With the command below we can check it.
python2 vol.py -f stuxnet.vmem connections
No connections were establishing when the memory was dumped. Now, we are going to see the ports that were listening in the computer.
In the picture bellow you will see a “lsass.exe” with Pid 680 is bound to Port 500 and 4500, while “lsass.exe” with Pid 868 and the another one with Pid 1928 are not listening in these ports. It seems again that the “lsass.exe” with the PID 680 has a normal behavior because this process usually listens on these ports.
python2 vol.py -f stuxnet.vmem sockets
DETECTING DLL
The “lsass.exe” process with PID 680 appears to be a normal process… What’s happened with the other ones?
With the command below, we can check that “lsass.exe” with Pid 868 and Pid 1928 have a load lower DLLs.
python2 vol.py -f stuxnet.vmem dlllist –p 680 | wc –l python2 vol.py -f stuxnet.vmem dlllist –p 868 | wc –l python2 vol.py -f stuxnet.vmem dlllist –p 1928 | wc –l
Also, we can detect that the process with Pid 1928 has unlinked DLLs.
python2 vol.py -f stuxnet.vmem ldrmoudles –p 1928
We can get more information about it with this command.
python2 vol.py -f stuxnet.vmem ldrmoudles –p 1928 -v
These kernel calls are directly related with stuxnet worm. See the URL below:
http://www.f-secure.com/v-descs/trojan-dropper_w32_stuxnet.shtml
DETECTING INJECTED CODE
The malfind command helps us to find hidden or injected code/DLLs in the user mode memory. Then we are going to export these DLLs and we will upload them to www.virustotal.com in order to check if an anti-virus detects them.
We already know that the process with PID 680 is normal. For this reason we will continue with the other ones.
python2 vol.py -f stuxnet.vmem malfind –p 868 –dump-dir evidences/
We can see two files have been created. We continue doing the same with the “lsass.exe” process with Pid 1928.
python2 vol.py -f stuxnet.vmem malfind –p 1928 –dump-dir evidences/
The next step will be to upload to www.virustotal.com these files in order to check if some anti-virus vendor detects them as malicious files. In order to not upload the files, we will obtain the sha256 checksum of the files and then we will search on the Virustotal website.
sha256sum *.dmp
Here, you have the links to Virustotal with the report of the files which have been analyzed:
https://www.virustotal.com/en/file/e97d61f7393ac5838a1800f3e9aa22c6205f4d7e2bde494573d35c57bc9b7819/analysis/
https://www.virustotal.com/en/file/163b7da37df4ae6dafbfb5bf88b319dabf7846cee73d4192c6a7593e835857a8/analysis/
https://www.virustotal.com/en/file/abce3e79e26b5116fe7f3d40d21eaa4c8563e433b6086f9ec07c2925593f69dc/analysis/
https://www.virustotal.com/en/file/2b2945f7cc7cf5b30ccdf37e2adbb236594208e409133bcd56f57f7c009ffe6d/analysis/
https://www.virustotal.com/en/file/10f07b9fbbc6a8c6dc4abf7a3d31a01e478accd115b33ec94fe885cb296a3586/analysis/
https://www.virustotal.com/en/file/a4b4b29f0df45283b629203b080c09ddb5bc6eb4cd8e9b725f75121a8b7e728e/analysis/
https://www.virustotal.com/en/file/2b2945f7cc7cf5b30ccdf37e2adbb236594208e409133bcd56f57f7c009ffe6d/analysis/
Notice that the majority of them have been detected as Stuxnet Worm
Source: http://www.behindthefirewalls.com/2013/12/stuxnet-trojan-memory-forensics-with_16.html












Nhận xét
Đăng nhận xét